What is hashing in cryptocurrency? Imagine a world where every digital transaction is a unique puzzle. Hashing is that cryptic piece ensuring no two pieces are alike, safeguarding your digital treasure trove. Think of it as a high-tech lock and key, crafted by complex math that turns your crypto data into a code no one can crack without the right sequence. It’s the backbone of blockchain security, a silent guardian standing firm against the threats in the digital realm. Whether you’re a budding crypto enthusiast or a seasoned pro looking to brush up on the basics, hold tight as we unlock the mystery of crypto security, one hash at a time. Let’s dive in and understand why this encryption technique is the unsung hero keeping your digital coins safe.
Demystifying Hashing in the Cryptocurrency World
Understanding the Crypto Hash Function Definition
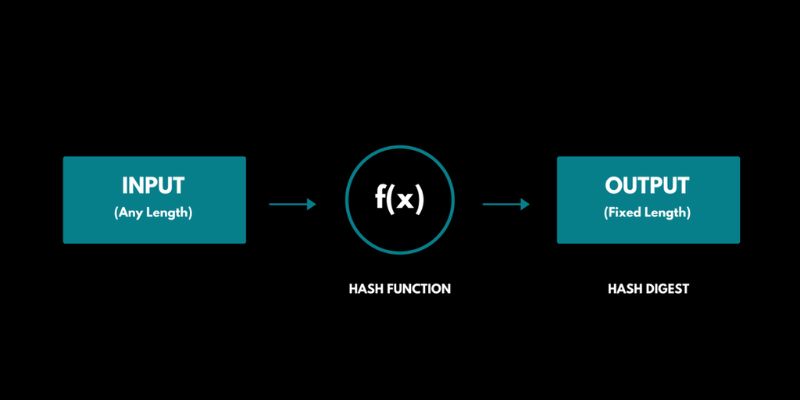
What’s a hash function in crypto, you ask? It’s a way to secure data. It’s like turning a secret note into a scramble of numbers and letters. No one can tell what your note said just by looking at this jumble. But, it’s special because changing even one tiny bit of your note makes a whole new scramble.
Imagine you’re baking cookies using the same recipe every time. Each batch, the cookies look and taste the same. That’s like a hash function. You put information in and get a unique cookie—or hash—out. But if you change the sugar to salt, you get a very different cookie.
A crypto hash function works like this but for digital data. You feed it any size data—like a message or transaction. It gives you a fixed-size hash. If anyone tries to change the info, the hash changes too. This lets everyone know something’s up.
The Cryptographic Technology Behind Hash Functions
Now let’s talk tech—cryptographic hash technology! It’s a big deal in making sure things in the crypto world stay safe. Here’s how it works. Take SHA-256, for instance. This secure hash algorithm munches on data and spits out a 256-bit hash value. That’s a mega long mix of numbers and letters.
Every hash value this makes is unique—like a digital fingerprint in crypto. Even if two people have almost the same info, their hash values won’t match. And that’s super important for proof of work and hashing in mining.
Miners use these hash functions to help secure the blockchain. They race to solve cryptographic puzzles using these functions. It’s a tough job that needs lots of computer power. The faster your computer, the more guesses—or hash rates in mining—you make every second.
Hashing doesn’t just keep the miners busy, though. It’s also all about transaction verification. Every transaction gets hashed. This keeps the records straight without spilling your secrets. Oh, and ever heard of a Merkle tree? It’s a smart way to organize lots of hash values in the blockchain. It makes it quick to check if a transaction is legit.
Why’s this hashing thing so important for security? The reasons are plenty! It fights off double spending and fakes with that unique digital fingerprint. It slams the door on tampering. And it makes sure every coin in your crypto wallet is the real deal.
So there you go—hashing in a nutshell. It’s a star player in keeping your digital money safe and sound. Thanks to these clever hash functions, we can trust the wild world of cryptocurrency a bit more each day.
The Backbone of Blockchain Security: Hash Algorithms
Exploring SHA-256 and Its Role in Cryptocurrencies
When I say “hashing,” think of it as making a unique digital fingerprint for data. For example, each time I write a sentence, a hash algorithm could turn it into a short set of numbers and letters. This is called a hash value. It’s like a data ID card. Hashing is a big deal in keeping cryptocurrencies safe.
The most common type is called “SHA-256.” It stands for Secure Hash Algorithm. What it does is crazy important. It turns input (like a file or a message) into a fixed-size string of characters. Every time you use SHA-256 on the same data, you get the same hash value back. But if you change the data even a little, you get a totally different value. This helps keep data safe and sound.
SHA-256 is used by Bitcoin and other crypto types. It’s a key part of mining, too. Miners work to find a hash that meets certain rules. When they do, they can add a new block of data to the blockchain.
What’s cool about SHA-256 is that it’s one-way. This means you can’t figure out the original data just from the hash value. It keeps your stuff super secure. And getting two sets of data to give you the same hash value (a collision)? Nearly impossible.
Merkle Trees: Ensuring Integrity with Hash-Based Data Structures
Now, you might wonder, “How do we check so much data quickly?” Enter Merkle trees. These are like family trees for data. But instead of names, they use hash values. Each ‘leaf’ is a piece of data, like a crypto transaction. Then pairs of leaves are hashed together, and this goes on until there’s just one hash at the top, called the root.
This is wicked smart because with the root hash, you can check if any piece of data is valid and unchanged. If even one bit is off, the whole tree’s hashes change. This is hashing and transaction verification in action. It’s perfect for blockchain, where every piece of data must be on point.
Use Merkle trees once, and you’ll get why they’re the backbone of crypto. They make things fast, too. Instead of checking every single detail, you just check the Merkle root. If this matches, you’re golden.
Merkle trees plus SHA-256 and you’ve got a power team. They work together in blockchain to make sure everything is correct and that crypto is what it promises to be: secure and reliable. Hashing isn’t just a part of the system; it’s the hero, keeping your digital coins safe every second.
The Nexus of Mining and Hashing in Cryptocurrency
Proof of Work: The Connection Between Mining and Hashing
Mining and hashing are best buddies in the world of cryptocurrency. They’re like the dynamic duo that keeps everything safe and sound. Hashing turns data into a set code. This code, or hash value, is like a secret name for data that only it has.
Mining is the process of making new coins and checking transactions. Miners use powerful computers to solve complex puzzles. These puzzles are actually hash challenges created by the crypto network.
When miners find the right answer to the puzzle, it means they’ve created a valid hash. This hash proves they did the work. That’s why it’s called “proof of work.” The miner gets new coins as a reward for this work. But that’s not all! They also help to confirm other people’s transactions. This makes the whole system works smooth and safe.
Nonce Values: The Unsung Heroes in Blockchain Hashing
Have you ever heard of a nonce? In crypto, it’s not what you might think! Nonce stands for “number only used once.” It’s a super important part of mining.
When miners are solving those tough hash puzzles, they use the nonce as their secret weapon. A nonce is a random or unique number added to the hash function. Why do we need it? Well, it helps make a special hash value that fits the rules of the crypto network.
Think of it like a special ingredient in a magic recipe. Without it, the hash just isn’t right. So miners keep trying different nonces until they find the exact right one that works.
When they do, it’s like they’ve struck gold! They can add a new block of transactions to the blockchain. This block is super secure because of the hashing and the nonce. It’s like a safety lock that keeps everybody’s coins safe and sound.
Nonce values are small but mighty. They help keep the whole crypto world in check. Thanks to noncies, no one can cheat the system. They ensure every block is unique and secure. This helps everyone trust the cryptocurrency they’re using.
So now you know about the power couple of mining and hashing. And the little hero nonce that keeps the crypto world turning! They all work together to keep our digital coins safe and make the magic of cryptocurrency possible.
Strengthening Blockchain Integrity with Advanced Hash Properties
Collision Resistance and Preimage Resistance in Cryptography
Let’s talk about how we keep crypto safe. Imagine your digital data as a unique pattern. A hash function scrambles it into a secret code. Like a secret handshake, no two should be the same. This is what we call collision resistance. It means even the smallest change makes a new, different secret code.
Now, think about getting this code without the original pattern. Sounds hard, right? That’s preimage resistance. It stops folks from working backwards to find your data. For crypto, this is key. It stops cheats from faking transactions or stealing coins.
Let’s say you had something basic, like “12345.” A strong crypto hash function hides it, spits out something like “a1b2c3.” If you change just one number to “12346,” the code becomes “d4e5f6.” Totally new. And you can’t guess “12345” from “a1b2c3” alone. Now, that’s a tough nut to crack!
Hash functions are your data’s bodyguard. They’re in everything: from checking if your files are safe to keeping your coins secure. They make sure what’s yours, stays yours.
From Digital Signatures to Smart Contracts: Hash Functions at Work
Now think, how do we sign things in the crypto world? Digital signatures! They’re like a promise that can’t be broken. When you sign a document, the hash function locks in your agreement. It’s a digital fingerprint that says “Yes, I agree” in code.
Smart contracts use the same magic. They’re like robot deals that self-execute when conditions are met. But how do they know the deal’s legit? You guessed it, hashing again. It checks everything’s in order before the robot deal kicks in.
This stuff is powerful. It makes sure you can’t say, “I was hacked!” or “I never said that!” once you’ve signed on the digital line. And for smart contracts, it’s like a guarantee. If all the secret codes match up, the deal’s good. No trust needed. It’s all in the code.
Hashing is more than a techie thing. It’s the unsung hero keeping crypto in line. It’s what makes sure when you “shake hands” on a deal, it’s as good as done. No take-backs, no tricks. Just honest agreement, kept in check by jumbles of letters and numbers. That’s our world, and that’s what we protect.
We’ve explored the secret sauce that makes cryptocurrencies tick: hashing. We started off by understanding what a crypto hash function is and the tech that drives it. Then we jumped into how hash algorithms like SHA-256 lay the groundwork for blockchain security and touched on Merkle trees that keep data in check.
We also saw how mining blends with hashing in this digital puzzle, where “proof of work” and nonce values play huge parts. Finally, we got into the nitty-gritty—collision resistance and preimage resistance that keep our blockchain safe and secure, and even peeked at how hashes power smart contracts.
Hash functions aren’t just tech jargon—they’re the vaults of the crypto world. They keep our digital gold safe, and as we’ve seen, they are mighty good at their job. And remember, it’s all about creating a chain that no one can break. That’s the raw power of strong hash properties in action! Keep these ideas in mind, and the next time you hear about hashing, you’ll know it’s all about keeping your crypto secure.
Q&A :
What exactly is “hashing” in the context of cryptocurrency?
Hashing in cryptocurrency refers to the process of taking an input (or ‘message’) and using a mathematical algorithm to produce a fixed-size string of characters, which is typically a sequence of numbers and letters. This output, known as a hash, is unique to the specific input data; even a small change in the input will produce a completely different hash. This is a foundational aspect of blockchain technology, used to secure and verify data integrity.
How does hashing contribute to the security of cryptocurrencies?
Hashing ensures the security of cryptocurrency transactions by creating a unique digital fingerprint for each transaction. When a block of transactions is created, it is hashed, and the hash is included in the next block, linking the blocks together in a secure chain. This makes it extremely difficult for any individual to alter transaction data without being detected, as changing any block would require re-mining all subsequent blocks due to the alteration of their respective hashes.
Can you reverse a cryptographic hash?
By design, a cryptographic hash function is a one-way function, which means it is computationally infeasible to reverse the process. This characteristic is known as pre-image resistance and is vital for security. It ensures that even if someone has access to the hash output, they cannot derive the original input data from it, providing a layer of security for sensitive data such as passwords and transaction details.
What hashing algorithms are commonly used in cryptocurrencies?
Several hashing algorithms are used in the cryptocurrency space, with some designed for specific coins. For instance, Bitcoin uses the SHA-256 hashing algorithm, while Ethereum initially used Keccak (SHA-3). Other notable hashing algorithms include Scrypt (used by Litecoin), X11 (used by Dash), and CryptoNight (used by Monero). Each algorithm has unique features aimed at optimizing security and performance for the cryptocurrency’s purpose and network.
Why is hash rate important in cryptocurrency mining?
The hash rate refers to the speed at which a miner or a mining network can perform the hash function. It’s usually measured in hashes per second (h/s). A higher hash rate increases a miner’s chances of finding the next block and receiving the mining reward. Consequently, the hash rate is a good indicator of the network’s security; as it increases, the difficulty of performing a 51% attack, where a user or group gains control of the majority of the mining power, becomes greater, thus ensuring better protection against tampering with the blockchain.