What is a Scam Coin? In the booming cryptocurrency market, Scam Coins pose a significant threat, designed to defraud investors. These deceptive assets promise high returns but ultimately lead to financial loss. Stay informed and protect yourself by learning how to identify and avoid these fraudulent schemes.
Understanding what is Scam Coins?
The cryptocurrency market has been expanding at an unprecedented pace, drawing the attention of investors worldwide. However, behind this rapid growth lies a hidden danger: Scam Coins—cryptocurrencies created with the sole purpose of defrauding investors and seizing their assets.
The hidden dangers of Scam Coins
Recent years have witnessed numerous incidents where individuals have lost substantial amounts of money by investing in Scam Coins. Notable examples include the infamous cases of Luna and TerraUSD, which resulted in billions of dollars in investor losses. These events underscore the importance of understanding Scam Coins and their associated fraudulent schemes to safeguard oneself from potential risks in the crypto space.
Scam Coins: The “Wolf in sheep’s clothing” of investments
Scam Coins are akin to a “wolf in sheep’s clothing.” They are often marketed with alluring promises of high returns and are presented with polished, professional images to deceive investors. The reality, however, is starkly different; the ultimate goal of Scam Coins is to siphon off the assets of their victims.
Top 10 Common Scam Coin tactics: Psychological manipulation and technical attacks
In the dynamic and often volatile world of cryptocurrencies, scammers employ various tactics to exploit investors. These tactics range from psychological manipulation to sophisticated technical attacks. Understanding these methods is crucial for protecting oneself in the crypto market. Below are ten prevalent scam coin schemes categorized into psychological manipulation and technical attack strategies.
Psychological manipulation tactics
Exit Scam
An Exit Scam is one of the most notorious forms of fraud in the cryptocurrency space. In this scheme, the developers of a project raise substantial funds from investors, only to suddenly disappear from the market, leaving investors with nothing. This tactic preys on the trust and financial commitment of the investors, capitalizing on their lack of control and oversight.
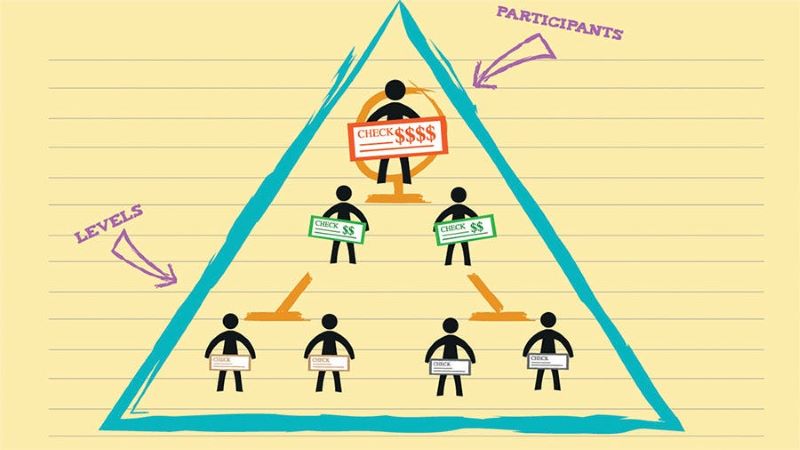
Ponzi/Pyramid Scam
Ponzi and Pyramid schemes are classic forms of fraud that involve using funds from new investors to pay returns to earlier investors. This creates an illusion of profitability and attracts more participants. However, when the flow of new investments slows down, the entire system collapses, leaving the last investors with significant losses.
Rug Pull
A Rug Pull occurs when a project’s developers abruptly remove liquidity from an exchange, causing the value of the cryptocurrency to plummet dramatically. This tactic prevents users from selling their assets and effectively wipes out their investments. It’s a deceptive method that exploits the trust placed in the project’s liquidity.
Pig Butchering/Romance Scam
Pig Butchering, or Romance Scam, involves scammers establishing a false romantic relationship with the victim. They then persuade the victim to invest in a fraudulent cryptocurrency project. Once the victim has invested, the scammers disappear with the funds, leaving the victim defrauded and financially devastated.
Social Engineering
Social Engineering involves manipulating psychological factors such as FOMO (Fear of Missing Out) to lure investors into making hasty decisions. Scammers create a sense of urgency or exclusivity around a project, convincing investors to act quickly without conducting proper due diligence, thereby facilitating potential losses.
Technical Attack Strategies
Phishing Attack
Phishing Attacks involve creating fake emails or websites that mimic legitimate services to steal personal information and account credentials. Victims are deceived into entering their details on these fraudulent sites, which are then used to gain unauthorized access to their cryptocurrency holdings.
Dusting Attack/Revoke Scam
A Dusting Attack involves sending a small amount of cryptocurrency to a victim’s wallet. The intent is to track the victim’s transactions and potentially trick them into interacting with fraudulent sites to “claim” their assets. This interaction can lead to the theft of the victim’s entire holdings.
Sybil Attack
A Sybil Attack involves creating multiple fake accounts to manipulate the market. This strategy inflates the value of a cryptocurrency by generating a false sense of demand or legitimacy, thereby attracting unsuspecting investors. It undermines market integrity and exploits investor trust.
DDoS Attack
Distributed Denial of Service (DDoS) Attacks involve overwhelming a project’s network with excessive traffic from numerous computers. This attack can cripple the system, leading to data loss and disruption of services. The resulting chaos can be used to exploit vulnerabilities or cover up other fraudulent activities.
Malware Attack
Malware Attacks involve installing malicious software on a victim’s computer to steal personal information and account details. This silent intruder can compromise security and lead to significant financial losses if the attacker gains control of the victim’s cryptocurrency assets.
Identifying Scam Coins: Prevention is better than cure
In the rapidly evolving cryptocurrency market, the rise of Scam Coins presents a significant risk to investors. Recognizing the signs of a Scam Coin is crucial for safeguarding your investments and avoiding financial loss. Prevention through diligent research and awareness is far more effective than dealing with the aftermath of a scam.
Here’s how to identify potential Scam Coins and protect yourself from falling victim to fraudulent schemes.
Unrealistic Promises of High Returns
Scam Coins often advertise unrealistically high returns with little to no risk. Promises of guaranteed profits or “get-rich-quick” schemes should raise immediate red flags. Legitimate investments come with risks and typically do not guarantee high returns without the possibility of loss.
Lack of Transparency
A legitimate cryptocurrency project will have a transparent team with verifiable credentials and a well-defined roadmap. Scam Coins, on the other hand, often lack clear information about the team, their qualifications, and their previous projects. Be cautious if a project’s whitepaper or website is vague or lacks detail.
Absence of a Solid Business Model
A credible cryptocurrency project should have a clear business model and use case. Scam Coins frequently lack a viable or coherent business plan, relying instead on hype and speculation to attract investors. Evaluate the project’s utility and real-world application before investing.
High Pressure Tactics
Scammers often employ high-pressure tactics to push investors into making quick decisions. This can include limited-time offers, urgency, or exclusive opportunities. Genuine projects typically provide ample time for due diligence and avoid pressuring potential investors.
No Verifiable Track Record
Check if the project has a history of successful past projects or partnerships. Scam Coins usually lack any verifiable track record or credible endorsements. Look for testimonials and third-party reviews to assess the legitimacy of the project.
Unusual Token Distribution Patterns
Scrutinize the token distribution mechanism. Scam Coins may exhibit suspicious distribution patterns, such as large allocations to the project team or a lack of liquidity for public trading. Transparent projects typically have clear tokenomics and equitable distribution models.
Anonymous or Fake Team Members
Research the team behind the project. Scam Coins often have anonymous or unverifiable team members. Reputable projects will have publicly identifiable team members with established professional backgrounds. Avoid projects where the team’s identity cannot be verified.
Inconsistent or Flawed Whitepaper
A well-written whitepaper is essential for understanding a project’s vision and technical details. Scam Coins often have poorly written or inconsistent whitepapers with technical flaws or unrealistic projections. Thoroughly review the whitepaper for clarity, feasibility, and technical accuracy.
Lack of Regulatory Compliance
Legitimate projects usually adhere to regulatory standards and provide information on compliance. Scam Coins may bypass or evade regulatory scrutiny, potentially operating in jurisdictions with weak oversight. Ensure the project is compliant with relevant regulations.
Negative Community Feedback
Pay attention to the cryptocurrency community’s feedback on social media and forums. Consistent negative reviews, complaints, or reports of fraudulent activity can be significant indicators of a scam. Engaging with the community can provide valuable insights and warnings.
For ongoing insights, follow Dynamic Crypto Network.